IT systems have evolved to the point where they can process a large amount of data in a short amount of time. At the same time, protecting them is growing more difficult. Information must be kept secure and accessible, and its integrity must be preserved, in order to enable safe processing. After all, if information begins to leak, it can lead to a trust issue and a competitive disadvantage.
Information security is becoming increasingly vital, especially in the age of Facebook, Twitter, and other social media platforms, but it is also becoming increasingly vulnerable to dangers. As a result, well-organized and clearly operational professional IT security management has become a critical requirement for businesses.
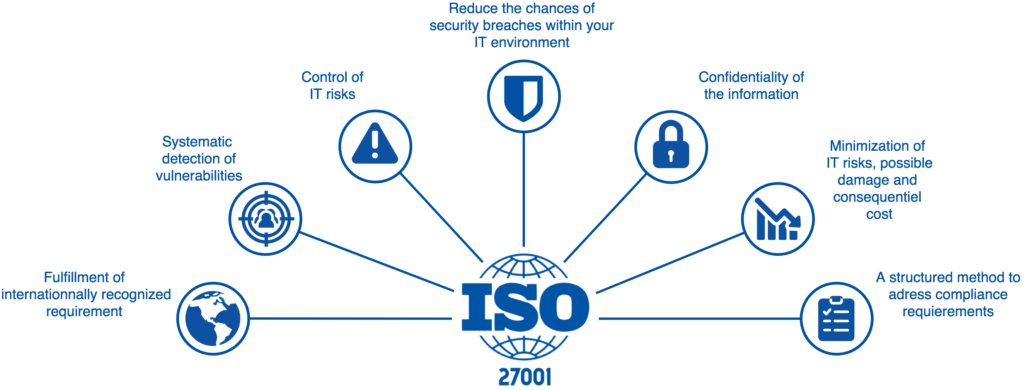
We provide you with an independent review of the degree of consistency of your information security management system (ISMS) to the ISO 27001 requirements with an ISO 27001 certification.
We examine the security of information and IT environments using ISO 27001, a globally recognized standard. It outlines the implementation requirements as well as the documentation for an ISMS. Security risks can be reduced, and IT security processes can be implemented to help you improve the quality of your systems over time.